 |
|
||
|
As Cisco says about SWAN:
"The Cisco Structured Wireless-Aware Network (SWAN) provides the framework to integrate and extend wired and wireless networks to deliver the lowest possible total cost of ownership for companies deploying wireless LANs (WLANs). Cisco SWAN extends 'wireless awareness' into important elements of the network infrastructure, providing the same level of security, scalability, reliability, ease of deployment, and management for wireless LANs that organizations have come to expect from their wired LANs.
From small businesses to large-scale enterprise multinational companies; within WLAN campus deployments or branch offices; at universities; in retail, manufacturing, or healthcare industries; or at hot spot locations, Cisco SWAN reduces overall operational expenses by simplifying network deployment, operations and management. With Cisco SWAN, several, hundreds, or thousands of central or remotely located Cisco Aironet Series access points can be managed from a single management console. Cisco SWAN's flexibility allows network managers to design networks to meet their specific needs, whether implementing a highly integrated network design or a simple overlay network."
Cisco shows this as an integrated approach with elements at all three layers of the Cisco network design model of core, distribution, and access layers.
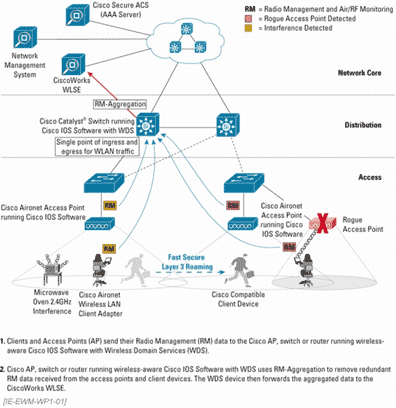
Figure 1.
Cisco lists the benefits of SWAN as:
Easier deployment through assisted site surveys
Ability to manage from a single location a few to thousands of access points located locally or remotely
Integrated security
Enhanced roaming ability
Radio interference troubleshooting
To achieve the full benefits of SWAN four components must be installed. These are:
Cisco Aironet access points
The Wireless LAN Solution Engine (WLSE)
An IEEE 802.1x authentication server
Client devices that support the Cisco Wireless Extensions
There is an extensive line of Aironet access points and client adaptors. These devices are discussed in another section of this tutorial. For SWAN compatibility, these access points must support the wireless features in the Cisco IOS.
A significant part of the SWAN initiative is the Wireless LAN Solution Engine. The WLSE is a combination of hardware and software in the form of a 1U Linux-based appliance that is placed in the network operations center. It is then connected to a Cisco Catalyst switch. The software allows a single management platform to control thousands of access points through a single web based interface. For example, Version 2.9 can support up to 2,500 access points in a single domain. More can be supported through multiple domains.
WLSE interoperates with the features provided by the Wireless Domain Services (WDS) software. WDS is a set of Cisco IOS features specifically for wireless devices. It provides the necessary software support for client mobility, deployment, and management. Unlike the other components of SWAN, WDS can reside in one of several locations, depending on the size of the wireless network. At this time the WDS runs on the Cisco Aironet 1230 AG, 1200, 1130 AG, and 1100 Series access points as well as the Catalyst 6500 Series WLSM-equipped switches. WDS can operate in these other devices because it uses its own control and data planes. Therefore, data handling rates are unaffected. Beginning in 2005, the features of WDS will be added to more devices such as routers and switches.
In the SWAN-enabled environment, WDS aggregates radio management information collected from access points and client adaptors and sends this information to the WLSE where it is used to manage, monitor, and control the RF environment. For interference and security management, the WDS takes the RF measurements made by the access points and forwards them to the WLSE for analysis. Based on this information, the WLSE can detect rogue access points, can detect interference from other devices, can provide assisted site surveys, and can adjust the devices for optimal coverage.
Fast Secure Roaming requires WDS because it eliminates the need for a reauthentication by an authentication server. This allows the speed of reassociation required for real time applications. WDS must be able to converse with the authentication server and the access points for this to function.
The WDS is a required component for full SWAN functionality. For deployments that use access point-based WDS, at least one WDS AP per subnet is required for RF management of that subnet. For deployments that use the Catalyst 6500 Series switch, access points located in different subnets can be supported by a single WLSM-enabled Catalyst 6500 Series.
The configuration of the WDS depends on the device on which it is running.
The Wireless LAN Services Module (WLSM) is a card that is placed in a Catalyst 6500 switch.

Figure 2.
The WLSM provides a common aggregation point for the data the access point radio management functions prepare for use by the WLSE. It provides a central key management system to help ensure security of client roams. It also provides authentication for 1100 and 1200 Series access points. Finally, it assists in client mobility management, such as layer 2 and 3 roaming.
This module is required for key components of SWAN such as:
Layer 3 roaming
Establishing different groups of users. Each group can be managed with their own set of access controls. For example, an employee can be provided with more access than a guest can. Up to 16 groups are currently supported.
Extending the 6500 switch's ability to provide denial of service, access control list, network intrusion detection, and VPN services to the wireless, not just the wired network.
Providing the ability to configure new devices.
Providing a single control point for all wireless traffic.
For full functioning, this card requires the Supervisor Engine 720. The combination of the Catalyst 6500, the Supervisor 720, and the WLSM is quite expensive. This is not a solution for a small to medium size operation.
Configuration of the WLSM is straightforward. After the module is inserted into the Catalyst 6500 switch, the WLSM is configured with a VLAN to communicate to the supervisor. Next, the supervisor is configured with a VLAN to communicate to the Catalyst 6500 Series WLSM with one tunnel interface per mobility group. Finally, the access point configuration is updated with the IP address of the Catalyst 6500 Series WLSM and each SSID is updated with a mobility group number.
Cisco lists several benefits for SWAN. The first of these is easier deployment through assisted site surveys. As a previous tutorial discussed, the site survey process can be lengthy and error prone. It is difficult to design a placement of access points in the typical building that provides both coverage over the entire building, while keeping the coverage to the building itself. The assisted site survey feature automates this by determining optimal access point settings including transmit power and channel selection. The WLSE-assisted site survey process includes five steps.
A floor plan is imported into the site survey tool.
Access points are provisionally located by hand on the diagram.
Aironet access points are installed at these locations in the building.
For the site survey, each access point is set to AP Scan Mode. Each access point operates on the same channel at maximum power. Each access point will detect its neighbors. The system will adjust the transmit power, frequency, and other required parameters to properly cover the building.
In the last step, the settings are fine-tuned in Client Walkabout mode. In this mode, someone walks around the facility with a client device. This device sends continuous measurements to the access points. This data is used to adjust the settings.
Operating costs are reduced because the changes and upgrades can be made in mass from a single point, rather than by having to physically visit each device. This is done by creating a policy template for each similar device.
With auto-configuration once a policy template is created using the template wizard, part of the WLSE, each device on the network can be set to that policy. Upon boot up, new access points receive the WLSE information via a DHCP server, then download the configuration information. Configuration templates based on device type, subnet located on, and required security parameters can be applied to access points. Once in place, these configurations can be monitored to ensure the devices conform to policy. A nonconforming device can be fixed from a single point.
Higher availability proactively monitors for performance and faults, such as detecting that an access point has failed. When failure occurs, the system compensates by automatically increasing the power and cell coverage of nearby access points.
Security is improved over that available in normal 802.11-based networks by the addition of the ability to detect, locate, and, to some extent, control rogue access points. Security holes are minimized by the ability to apply a consistent set of security policies to all access points.
Sources of RF interference can be detected so they may be removed. In addition to detection, the SWAN-enabled components will home in to the area where the interference is coming from.
SWAN can be viewed as having three levels of finer and finer control over the wireless side of the network and integration of that with the wired network. At the most basic level are Cisco wireless devices and those devices that support the Cisco Wireless Extensions. Next are Cisco access points acting as WDS servers. Finally, there is the full SWAN implementation where the wireless and wired devices are integrated into a seamless network through the WLSE and a WLSM-equipped 6500 series switch.
With standalone access points all of the standard security measures, such as WEP, WPA, EAP/802.1x, are supported. Client adaptors that support the Cisco Wireless Extensions allow the use of a wider range of EAP types.
Parts of SWAN can also work with just access points. When an access point is deployed in SWAN, non-switching mode layer 2 Fast Secure Roaming and local 802.1x authentication are supported. This mode requires the access point to be run as a Cisco WDS server. In non-switching mode, the wireless infrastructure is protected against external attacks, such as rogue access points and non-802.11 interference.
When a Catalyst 6500 is deployed, the access point is used in SWAN central switching mode. In this mode, the WDS server function is moved to the switch. SWAN switching mode adds centralized management and Fast Secure Roaming.
A key feature of this initiative is the ability to authenticate not just users, but access points as well. Once this is done, the communication between the WDS server and the WDS-enabled access point is secured.
Any 802.1x authentication server will work with SWAN. Of course, Cisco prefers their Access Control Server (ACS). As with most authentication servers it can control who uses the wireless network, set the privileges for each user, and record audit and accounting information.
Any Wi-Fi certified wireless client device will operate at a basic level in the SWAN-enabled wireless environment. For full support, especially the monitoring and security capabilities the adaptor must be a Cisco device or one that supports the Cisco extensions. The list of devices that support the Cisco extensions is not extensive. The current listing shows only 51 devices from 15 companies. Dell and Toshiba account for most of these.
[IE-EWM-WP1-D03]
[2005-02-22-01]
|